Institutional crypto staking has rapidly shifted from an experimental source of yield to one of the most important pillars of modern digital asset management, and what once sat at the edge of institutional crypto activity now stands at the centre of long term portfolio planning. As more professional investors adopt native staking at scale, expectations have changed significantly. For example, institutions no longer look for simple reward generation but they expect precise governance, controlled workflows, reliable staking infrastructure and reward streams that fit neatly into their internal risk models.
In this article co-authored by Matthew Felice Pace, CEO of Simply Staking, and Pavel Sivayeu, CTO at Aetsoft, we explain how institutional staking works, why it now plays such an important role in digital asset strategy, the key risks every organisation should understand and a practical 12-point checklist for selecting a trusted staking partner. Our goal is to offer you a clear and verifiable guide for any institution looking to expand or professionalise its staking operations in 2026.
What Is Institutional Crypto Staking?
First of all, before diving into the topic, it is worth defining in simple terms what is staking crypto? Crypto staking is the process of locking digital assets into a proof-of-stake blockchain so that they can help secure and operate the network. In return for contributing to this network activity, users receive staking rewards that are issued by the protocol. It is one of the most common ways for token holders to earn passive income while supporting the health and stability of the blockchain.
So what is institutional staking?
Institutional staking builds on the same concept but at a far greater scale as instead of having individuals staking their own holdings, large organisations would lock cryptocurrency assets into proof-of-stake networks in exchange for staking rewards. For the most part, these organisations have very different requirements from retail users. One of the main differences is that institutions rely on policy controlled workflows, enterprise grade infrastructure and audited security processes to manage staked assets at scale. Furthermore, they also require strict record keeping, full transparency and clear governance over how staking operations are executed. For this reason, institutions typically delegate their holdings to custodians or specialised staking providers rather than relying on simple exchange wallets, as this approach supports enterprise level standards, including internal verification processes, multi approval workflows, hardware security modules and independent audits. Institutional staking therefore combines active blockchain participation with the level of risk management expected in corporate environments.
At its core, institutional staking is still a very simple concept. Assets are locked on-chain, validators help secure the network and the protocol distributes new tokens as rewards. These rewards can support long term portfolio growth while also giving institutions a degree of involvement in protocol governance. Considering this, it is no surprise that the scale of institutional involvement has grown significantly and staking now forms a core pillar of professional digital asset strategies, especially for organisations that hold large reserves of staked tokens or staked assets on behalf of clients.
Staking Mechanics: How Institutions Approach Yield Generation
Institutions engage in crypto staking with clear processes, detailed controls and specialist infrastructure. Their staking approach focuses on maximising yield while ensuring that all operations remain compliant, auditable and secure. To do this, institutions focus on three main areas: custody choices, policy controls and protocol specific requirements. These elements work together to shape how institutional staking functions in the real world.
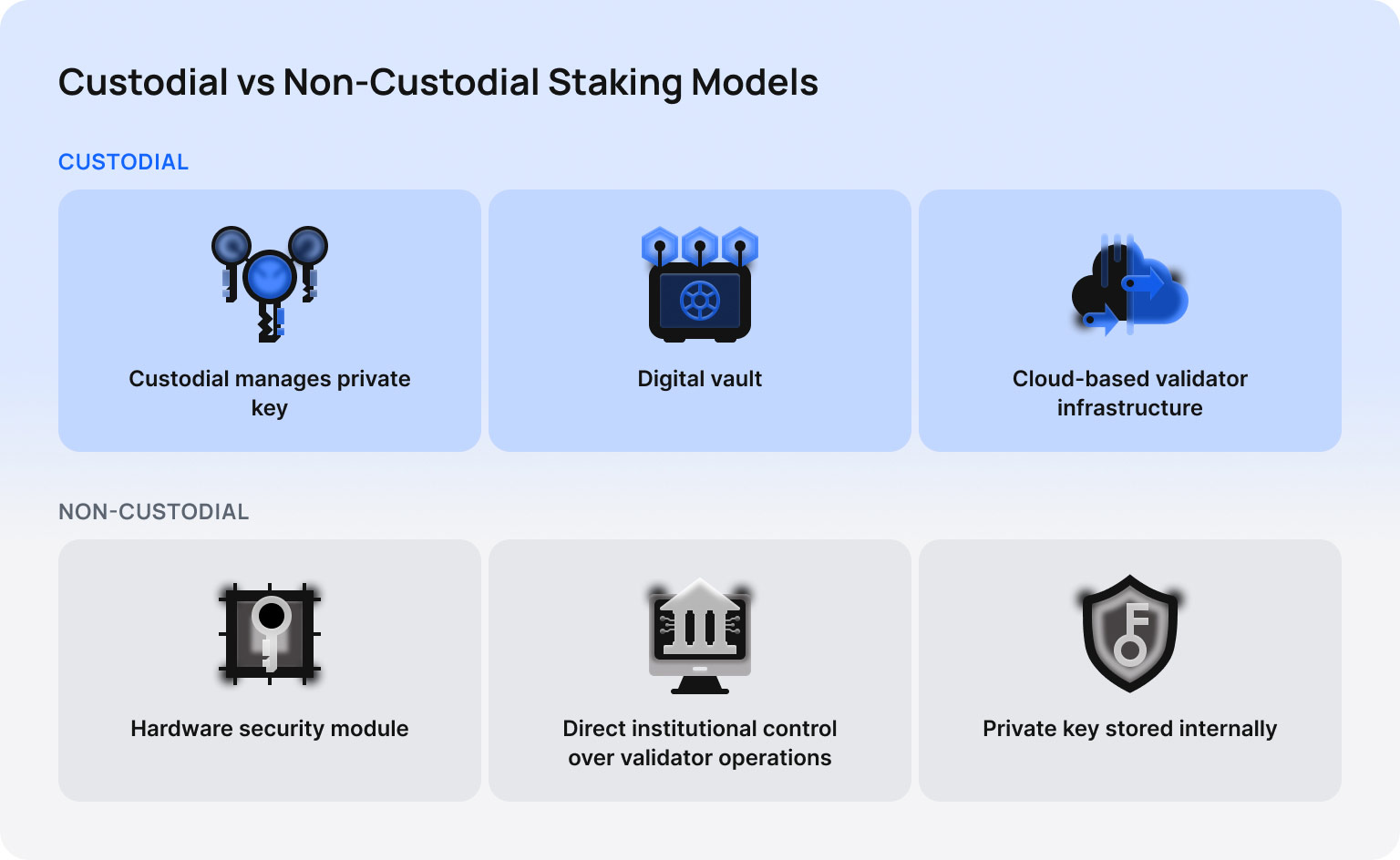
Institutional crypto staking usually follows one of two models, and each model offers its own set of advantages and trade offs.
Custodial staking places responsibility for asset management into the hands of a trusted custodian. This simplifies operations because the custodian manages private keys, validator connections and reporting. Institutions that use custodial models can rely on secure external infrastructure while maintaining full oversight of their staking activities, and therefore, this approach is often chosen by organisations that prioritise operational simplicity, detailed reporting and strong governance controls.
Non-custodial staking gives the institution direct control over private keys while delegating only the validator operations. In practice this requires more advanced internal systems because keys are held in secure vaults or hardware security modules. Although this allows maximum control, it also requires mature operational capacity and clear governance structures.
It is worth noting that frequently, institutions adopt hybrid arrangements where validators run externally while asset access remains governed internally through strict approval workflows.
The Role of Off-Chain vs On-Chain Policy Controls
Institutional staking involves both off-chain governance and on-chain protocol rules. Off-chain controls include corporate policies, multi-tier approvals and role based governance systems to ensure that no staking operation can occur without appropriate review. Nowadays, many institutional providers offer advanced approval workflows and policy controlled staking environments that are built specifically for enterprise level security needs.
When it comes to on-chain controls, these come directly from the protocol. They define the rules for slashing penalties, lock-up periods, reward distribution and how validators are chosen. Institutions then combine these protocol rules with their own internal governance to create a safe and compliant staking setup. The off-chain procedures guide how teams inside the organisation operate, while the on-chain rules ensure that validators behave in line with the network.
Understanding Protocol-Specific Lock-Up Periods and Requirements
Different networks impose different lock-up periods, minimum stake amounts and unstaking timelines. Institutions must plan carefully around these liquidity constraints because lock-up rules have a direct impact on capital flow and overall risk exposure. For example, some networks support rapid unbonding while others impose multi-week delays. Institutions therefore structure their staking strategy around these timelines, often spreading positions across several chains to balance yield, liquidity and operational flexibility.
Understanding network rules also means recognising how validator behaviour influences rewards, penalties and overall security. Institutions must be aware of minimum stake requirements and any validator obligations set by the protocol. To manage this effectively, teams need clear internal documentation and strong communication with their staking provider so that every protocol requirement is consistently met.
Benefits of Institutional Staking Strategies
Institutional crypto staking offers a range of advantages that extend far beyond simple yield.
First of all, one of the most important advantages is the predictable income stream that staking rewards can provide. Institutions can earn steady returns on assets that would otherwise sit idle, effectively turning long term holdings into productive capital.
Another key benefit is inflation protection. Many proof-of-stake networks mint new tokens to reward stakers, and therefore by participating in staking institutions would have the ability to offset dilution and help maintain the purchasing power of their holdings.
Crypto staking also reduces counterparty risk. Unlike lending or complex decentralised finance strategies, native staking rewards come directly from the protocol, and hence minimising exposure to third party defaults.
Additional benefits include stronger participation in governance, diversified income streams, improved portfolio stability, and enhanced reputation for supporting decentralised infrastructure. Many institutions see staking as a way to support the networks they invest in. Furthermore, it allows them to align with the values of those ecosystems while also contributing to their long term health and decentralisation.
Together, these advantages illustrate the broad benefits of crypto staking and show why staking has become an essential component of institutional digital asset strategies.
Risks of Staking
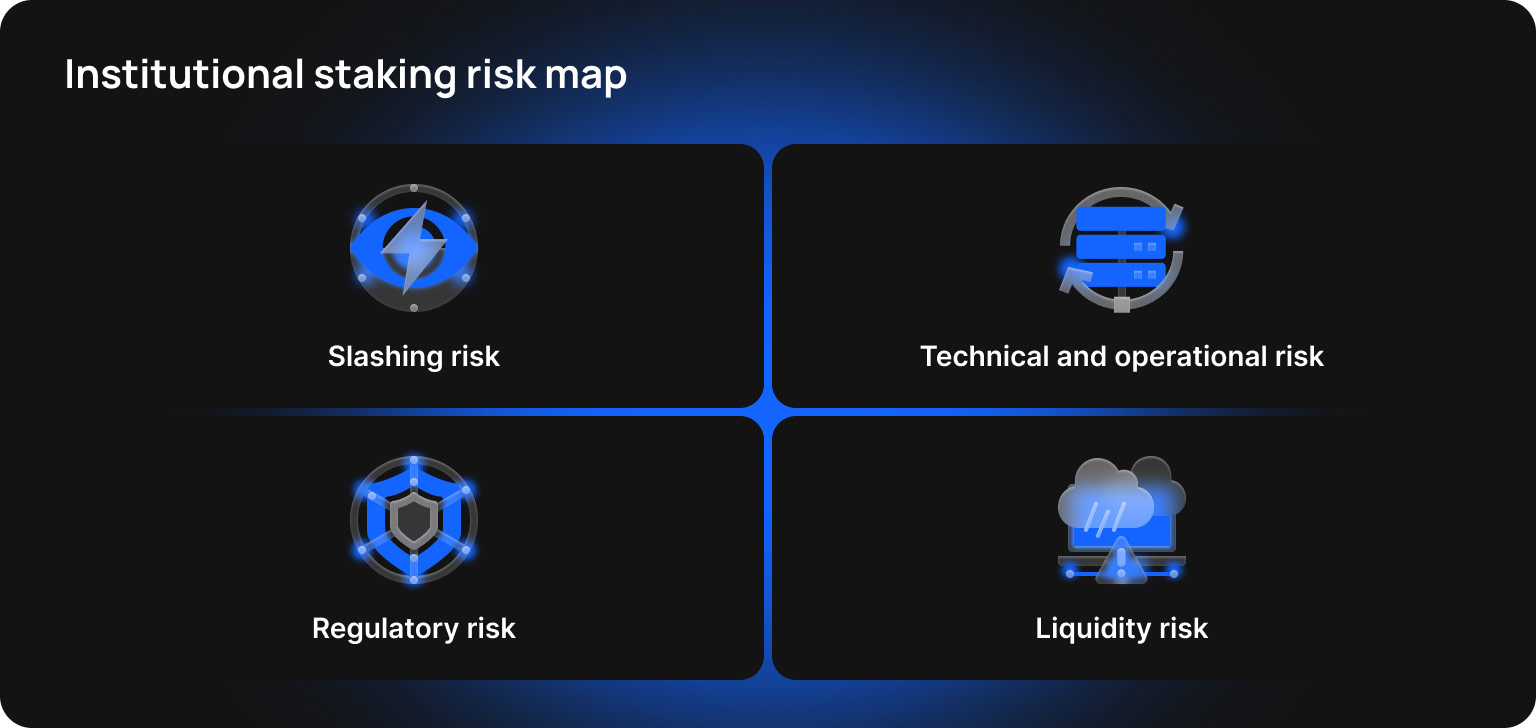
Despite its advantages, institutional staking also introduces several important risks that need to be understood and carefully managed, whether an organisation is choosing a staking provider or running its own validator infrastructure.
Slashing Risk: Assessing Loss Exposure and Vendor-Provided Insurance
Determine how often you’ll convert between cryptocurrencies and fiat. Frequent or automated conversions will require robust on/off-ramp integrations and more complex infrastructure. Occasional transactions can rely on simpler manual systems.
Also, define whether payments will be processed individually (gross) or in batches (netted). On Ethereum, for example, ERC‑4337 smart contracts allow batch transactions through Account Abstractions, which is a powerful feature that also introduces added risk.
Technical and Operational Risk: Downtime, Security Exploits, and Infrastructure Failures
Infrastructure failures are one of the most common causes of lost staking rewards. Validators need continuous uptime and secure environments to perform reliably. Hence it makes sense why institutions prioritise multi-region redundancy, strong hardware security, intrusion detection and 24 hour monitoring for mission critical staking operations. Even short periods of downtime can reduce rewards and, in some networks, may also lead to penalties. For this reason, many institutions choose to outsource validator operations to professional staking providers who specialise in maintaining reliable, decentralised and secure validator clusters.
Regulatory and Compliance Risk: KYC and AML Requirements and Evolving Securities Guidance
Institutions face strict regulatory requirements even when staking digital assets. Staking platforms must therefore support full compliance standards, including know your customer checks, anti-money laundering policies and financial reporting that meets the expectations of auditors and regulators. As guidance continues to evolve across different jurisdictions, institutions need to work with providers that maintain strong compliance teams, deliver regular audit ready reports and understand how regulatory changes may affect staking rewards, tax obligations or the classification of digital assets.
Liquidity Risk: Managing Capital Access During Unbonding Periods
When assets are staked, they become temporarily illiquid. Many protocols impose withdrawal periods that can limit access to capital, which in turn creates potential cash flow challenges. Institutions therefore need to plan carefully for unbonding windows and maintain sufficient liquidity buffers to support operational needs during these periods. Some organisations use liquid staking solutions for added flexibility, although these come with their own counterparty considerations.
Liquidity risk becomes even more significant when large holdings are involved, since any delay or market movement has a greater impact, which makes careful liquidity planning a crucial part of every institutional staking strategy.
The Vendor Selection Imperative: A 12-Point Institutional Checklist by Aetsoft and Simply Staking
Choosing the right staking provider is one of the most important decisions an institution will make. The downloadable 12-point checklist below created in collaboration between Aetsof and Simply Staking highlights the key areas that determine whether a provider is truly ready to support enterprise level staking.
Let’s have a quick overview of the main important points.
Security: Policy Controls, Key Management, and Audits
Security is the foundation of institutional crypto staking. Institutions should only work with providers that implement hardware security modules, multi-party computation, strict role based access control and documented key management procedures. Providers must also demonstrate that private keys never exist in a single unencrypted state, which includes clear key ceremonies, proper separation of withdrawal keys and rigorous internal approval processes.
Audits are equally important. A reliable provider is one who undergoes regular third party assessments such as SOC 2 or ISO 27001. Additionally, institutions should request audit summaries and evidence that operational controls are consistently applied.
Furthermore, insurance coverage is another essential consideration. Providers should maintain protection against theft, operational errors and slashing events. Institutions also should always review coverage limits and identify any exclusions to understand exactly what is protected.
Compliance: Regulatory Framework and Reporting Capabilities
Compliance readiness is a non-negotiable requirement. Providers must operate within clear regulatory frameworks and meet all relevant licensing obligations. Institutions should verify that a provider performs full identity checks, sanctions screening and can deliver audit ready reports for all staking activity.
A strong provider also supplies reliable reward breakdowns, fee summaries, transaction logs and proof-of-reserves information or equivalent attestations. These reporting capabilities help institutions maintain accurate accounting records and prepare any financial statements or tax filings related to staking rewards.
Infrastructure: Uptime, Decentralization, and Blockchain Agnosticism
Strong infrastructure is essential for safe and efficient staking. Institutions should only partner with providers that can deliver near perfect uptime and maintain validators across multiple regions. In turn, validators should operate in independent data centres with geographic diversity, multiple client implementations and dedicated fallback systems. It is also very important to work with blockchain agnostic providers that support a wide range of proof-of-stake networks as this adds flexibility to portfolio strategies and removes the operational burden of dealing with several different providers.
Performance monitoring is another key requirement. Providers should offer real time dashboards, alerting tools and analytics that track validator performance, slashing events, network participation and reward flow.
Service: Pricing, Support SLAs, and Expertise
Service quality is just as important as technical capability. Institutions should examine pricing structures carefully and ensure that fees are transparent and aligned with industry standards. Hidden fees or unclear commission models are clear warning signs.
Additionally, service level agreements should include guaranteed response times, clear escalation paths and round the clock support. Providers should also offer dedicated account managers who understand the institution’s portfolio and can provide ongoing strategic guidance. A strong provider will go further by offering educational support, sharing regular insights, participating in validator governance across networks and helping institutions align their staking strategy with wider market conditions.
A full PDF version of the institutional staking checklist is available for download here and can be used by compliance teams, risk officers and digital asset managers when assessing potential staking partners.
The Future of Institutional Staking
By 2026, institutional crypto staking has become a core part of professional asset management. Staking is no longer viewed as a secondary option but as a standard treasury practice for any institution holding digital assets at scale.
Growing adoption, stronger infrastructure and clearer regulatory guidance have helped staking evolve from a niche activity into a central pillar of the digital asset ecosystem. Institutions now regard staking rewards much like bond yields or dividend income, offering steady returns that support long term portfolio resilience.
As more networks adopt proof-of-stake security models, demand for high quality infrastructure will continue to increase. Providers that combine strong technology, robust compliance capabilities and clear communication will be best positioned to lead the next phase of institutional staking growth.
Final Thoughts
Institutional staking is becoming a central part of digital asset management, and organisations are increasingly looking for partners who can support secure, compliant and scalable participation in proof-of-stake networks. Aetsoft brings deep experience in blockchain engineering, smart contract development and secure workflow design, all of which help institutions build or refine the systems that underpin their staking operations. Their work in areas such as smart contract development and broader blockchain architecture offers a strong foundation for teams looking to strengthen or modernise their technical capabilities.
Simply Staking complements this with institutional grade validator infrastructure and a focus on long term reliability across multiple proof-of-stake networks. Through its dedicated approach to secure and transparent staking operations, Simply Staking helps organisations participate confidently in the networks they rely on.
Together, Aetsoft and Simply Staking are able to provide a combination of technical depth and operational stability that can support institutions as they integrate staking into their wider digital asset strategies. Whether teams are assessing providers, building internal processes or preparing to scale, this collaborative approach offers a practical path forward.
For those exploring their next steps, we highly encourage you to download the full institutional staking checklist from here.







